Researchers have uncovered a database shared on an underground forum containing more than 2,300 compromised Zoom credentials.
The database contained usernames and passwords for Zoom accounts – including corporate accounts belonging to banks, consultancy companies, educational facilities, healthcare providers and software vendors. Some of the accounts included meeting IDs, names and host keys in addition to credentials.
“One of the more noteworthy findings in [our analysis] is the stark increase in chatter concerning vulnerabilities and exploits pertaining to video conferencing and collaboration tools in deep and dark web forums,” said researchers with IntSights, in a Friday analysis. “Realizing most of the workforce is now required to do their jobs from home, threat actors are actively looking for ways to gain access to collaboration and communication tools, like Zoom.”
Etay Maor, chief security officer at IntSights, told Threatpost that the source of the credentials is unknown, but the smaller number of them suggests they didn’t come from a Zoom database breach. More likely, they came from small lists and databases kept by other companies/agencies.
“This specific database was just shared [as opposed to sold],” Maor told Threatpost. “Typically prices of databases are not very high anyway unless it is a very targeted database (one that resulted from a breach).”
The stolen credential discovery comes amidst the wave of remote workers driven home by the coronavirus pandemic, who have come to rely on online collaboration tools like Zoom and other platforms.
Compromised Zoom credentials could give cybercriminals access to web conference calls, where sensitive files, intellectual property data and financial information are shared. Cybercriminals can also use these credentials for social-engineering purposes, said Maor — ultimately leading to attacks like business email compromise efforts.
“If the attacker can identify the person whose account he has taken over (and that doesn’t take too much time – just use Google and LinkedIn), then the attacker can potentially impersonate that person and set up meetings with other company employees,” he told Threatpost.
Attackers can also use these types of compromised credentials to launch denial-of-service attacks, where they could “just join meeting and blast music or videos to interfere with the meeting,” said Maor. This practice, called “Zoom bombing,” has been spiking upwards over the past few weeks, despite the FBI cracking down on the issue and warning that those who take part in Zoom bombing could face jail time.
This finding by IntSights isn’t the only incident. Earlier this week security firm Sixgill reported that a dark web forum posted a link to a collection of 352 compromised Zoom accounts (including email addresses, passwords, meeting IDs, host keys and names, and the type of Zoom account). And, an ongoing phishing campaign emerged this week using a recycled Cisco security advisory, aimed at stealing victims’ credentials for the Cisco’s WebEx web-conferencing platform.
Credential Stuffing
Researchers with IntSights noted that several posts and threads in the underground forums were discussing different approaches for targeting Zoom’s services. A common attack vector discussed was credential stuffing, a type of brute-force attack where usernames and passwords are tested against a website in an automated way, in an attempt to take over the account.
“One issue that is worth noting is that many people tend to have a ‘strong password’ – one which has a combination of upper/lower case characters, numbers special characters, etc.,” Maor told Threatpost. “Unfortunately, once a person has such a strong password, they find it hard to have a unique one for each site and then they tend to reuse that same password. This means you don’t need special databases to conduct credential-stuffing attacks. You can simply use one of many large databases (Like “Collections 1-5”) and attempt to access Zoom, or any other service, with the usernames and passwords from that database.”
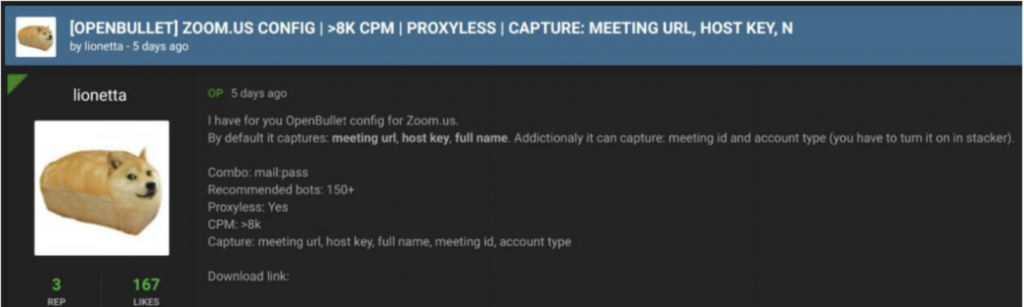
Of note, one of the forums suggested using OpenBullet for Zoom-related credential stuffing, which, according to the OpenBullet GitHub page, is a web testing suite that can be used for scraping and parsing data, automated pen testing and more.
“OpenBullet is just one of several easy-to-use open source tools that streamline the process of credential stuffing,” said researchers. “Cybercriminals have shared configuration files in the past for targets like Ring. While there are different techniques to counter credential stuffing, like using CAPTCHA, requiring two-factor authentication and limiting the number of login attempts from a specific IP or for specific time intervals, these impose a burden on performance and user experience.”
Researchers also warned users to stay on the lookout for bad actors spoofing web conferencing and virtual collaboration apps. In general, attackers are taking advantage of the panic around the coronavirus with phishing emails around financial relief, promises of a cure and symptom information details.
While researchers have discovered several security issues in the Zoom platform over the past weeks (from security flaws to privacy issues), Zoom has taken steps to bolster its security. That includes hiring former Facebook CISO Alex Stamos this week to provide special counsel.
“Researchers have already reported about multiple vulnerabilities in these tools,” said IntSights researchers. “Unfortunately, some users ignore even the most basic security measures, like securing online meetings with passwords or PIN codes – or even publicly showing their meeting ID, as seen in the case of the British government – which in turn allow attackers to take advantage of the situation.”
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.